Expected increase of HTTPS in 2018 realized
22 January 2019
Many developments have happened in the international SSL market as well as at Xolphin. 2018 was a turning point for the use of SSL: for the first time ever, there are more secure websites than insecure websites. Early last year, a large increase of HTTPS use was expected, leading to secure connections being the new standard. One year later, this appears to be a realistic estimation: by now the top 100 websites worldwide use HTTPS. Between 70% and 80% of all pages are loaded over HTTPS, and by June 2018, 32.6 million SSL certificates were in use globally. This is an increase of 68% compared to 2017, and 500% compared to 2016! Let's take a look at other interesting developments in 2018.
Impact of the new privacy law
The introduction of the GDPR in May had a lot of impact on European SSL use. The new European privacy law has been in effect from May 25, 2018. This new privacy law made SSL obligatory for all European websites that collect data. Almost every website has an input field like a login field or a contact form. Handling customer data without encryption and without an SSL certificate now has serious consequences.
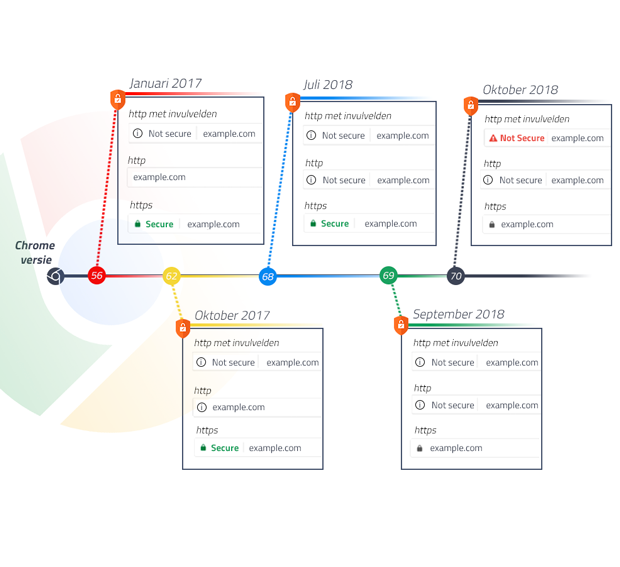
Changes in the display of HTTPS in Chrome
Google gave the use of SSL a boost by increasing visibility of warnings for websites without HTTPS. From July 2018, Chrome warns for insecure connections. In early 2017, Chrome started showing a 'secure' notice for websites with HTTPS. Google stopped displaying this 'secure' notice in September 2018, and replaced it with a warning for insecure websites instead: now a ‘Not Secure’ warning is shown for all insecure websites. This warning will become more visible over time. Nowadays, most browsers display warnings for insecure websites and insecure input fields.
SSL certificate use per type
Low-cost DV (domain validation) certificates are used most: about 94% of all issued certificates are DV certificates. Certificates with company data are often used by (larger) websites with more visitors. The use of DV, OV (organisation validation) and EV (extended validation) certificates is 38%, 49% and 13% respectively. This difference is even more significant for e-commerce websites, whose use of certificates with company data is 66% (of which 50% uses OV certificates, and 50% use EV certificates). Besides this, the validity period of all SSL certificates is limited to 2 years form March 2018, and TLS version 1.3 was released in August 2018.
The use of SSL for phishing websites has increased rapidly the last year. DV certificates without company data have the least strict issuance process, and are either free or very low-cost. Therefore, they are often used for phishing purposes. Research shows that more than half of all phishing websites use HTTPS. The HTTPS connection gives phishing websites a misleading, trustworthy appearance. The issuance process and validation for EV certificates is much more strict. This strict validation process minimizes the chance of abuse by phishing websites. To empower the importance of certificates with company data, multiple CAs established the London Protocol in June 2018.
In the Netherlands, the use of EV certificates has more than doubled over the last three years. Sectigo (formerly Comodo) has the biggest share in this with almost 70%. Whereas the main users used to be financial - and ecommerce websites, we now see an increase in use by SME’s.
Transition from Symantec to DigiCert
All Symantec, GeoTrust and Thawte certificates issued from the old Symantec infrastructure - before December 1, 2017 - are not trusted anymore since late 2018. The exact date differs per browser. After this date, certificates will trigger an error when visiting a website with an old Symantec certificate. Currently, the Certificate Authority DigiCert takes care of issuance of Symantec certificates. Do you still have valid certificates issued before December 1, 2017? You can reissue them free of charge.
Comodo continues as Sectigo
From November 1, 2018, Comodo CA is called Sectigo. This applies to the company name and all brand and product names. To ensure a smooth transition, the name ‘Sectigo, formerly Comodo CA’ will be used in 2019. Despite the new name, not much else will change. All certificates will continue to work. No adjustments or new installations are needed, and all certificates will still be trusted by browsers and applications. New trust logos based on the new logo are available, and from January 14 a new intermediate certificate will be used.

Developments at Xolphin
Xolphin is growing rapidly and is actively working on international expansion, especially in Western Europe and Scandinavia. In 2018, we have invested in further professionalization. Our ISO 27001 certification and WebTrust certification have been extended with an ISO 9001 certification. These new certifications ensure even more strict quality management and guidelines for certificate validation. Due to our rapid growth, we moved to a more spacious office in a central location in Alkmaar in March last year. This also gave us the opportunity to expand our team: the finance, development and validation departments have expanded considerably. Today, the validation team is able to validate in 11 different languages, which is necessary to optimally serve our international clients. The new office also gives us more space to offer internships to students. To maintain a high service level outside the Benelux area, we now have several local people employed in other European countries.
What will happen in 2019
The CA Security Council, a partnership between many large CAs, predicts at least 90% of all web traffic will be using TLS by the end of this year. The outdated encryption protocols TLS 1.0 and TLS 1.1 will be deprecated, starting early 2020. By then, TLS 1.2 will become the new standard. The use of TLS 1.3 will be actively stimulated. The CA Security Council expects a 30% increase of TLS 1.3 use in 2019.
The use of ‘encrypted phishing’ with free certificates is expected to continue to rise. This makes certificates with company data, providing an identity guarantee aside from encryption, even more relevant. That being said, the way browsers intend to display SSL certificates is quite interesting, especially considering the confusion already caused by recent changes in browsers. It would be beneficial if all browsers show similar messages depending on the SSL certificate validation level.
Our websites
SSLCheck
Our SSLCheck will examine your website's root and intermediate certificates for correctness and report any potential issues

