CAA DNS Records
The CAA record is a DNS record type that allows domainname owners extra control over SSL certificates that can be issued for their domains. You define which CA is allowed to issue what type of certificates, if any, for your domain. The CAA record type has been defined in 2013. Although the usage of CAA was quite common, it wasn't required until recently. Starting from September 2017, Certificate Authorities are required to check the CAA-record as part of the issuing process. It's not required for the domain owner to maintain a CAA-record.
What is a CAA record?
CAA records, an abbreviation for Certificate Authority Authorization records, are designed for specifying certificate authorities allowed to issue SSL certificates for a specific website. Not explicitly allowed certificate authorities won’t issue a certificate, while allowed CA’s specified in the CAA record can. Considering a certificate is affiliated with one certificate authority only, a domain owner is able to control which certificates can be issued to prevent abuse.
For example, by using the following record for xolphin.com, we restrict allowed certificate authorities to Sectigo/Comodo only:
IN CAA 0 issue "comodoca.com"
or
IN CAA 0 issue "comodo.com"
Domain owners are able to add multiple CAA records to the DNS, to allow multiple certificate authorities to issue certificates for the respective domain name. Adding a CAA-record isn't obligatory, while checking the records by the CA's is mandatory.
What are the advantages of CAA?
CAA DNS records allow for taking control of certificate authorities allowed to issue certificates for a specific domain, without required cooperation by the certificate authority. Furthermore, globally making use of CAA allows certificate authorities to contact a domain owner regarding a failed certificate issuance request. Because of this, domain and website owners will get insight in false or fraudulent certificate requests. Do note however, that using CAA records don’t restrict you to one specific certificate authority. Like mentioned earlier, making use of multiple CAA records allow for multiple certificate authorities to issue certificates for your domains.
Are there any disadvantages to using CAA?
- Checking for CAA records by certificate authorities is optional until September 2017. From September 8, 2017 onwards, certificate authorities are required to check the CAA record;
- Considering DNS itself is not a very secure system and has the potential to be bypassed, it is recommended to use DNSSEC. DNSSEC allows for an extra layer of security by adding a digital signature to a domain name;
- In case a CAA record is used, a delay could occur as the certificate authority has to check the CAA record. In case the CAA record doesn’t match up, the certificate authority may refuse the issuance request and ask for you to alter the records. This makes it, especially within larger organisations, important to fine tune the regulations on certificate management. This tool makes it easy to look for all the certificates issued for a domain.
How to configure CAA
CAA is a specific DNS record type that has to be supported by your DNS-manager. In many cases this is the registrar (the party used to register your domainname) or your hosting provider that hosts your website. Quite often you'll find older versions of DNS servers, that have no support for CAA, but there is a clear rising line in supporting hosting parties for CAA and hence the use of CAA records.
A CAA record has the following structure:
flag tag ca
- 'flag' can only contain 0 or 128, 0 defines the record as mandatory, 128 makes it optional. We advise for now to set it to '0'
- 'tag' sets the type of CAA record, it can either contain issue, issuewild or iodef. This defines the following options;
- 'issue' allows the CA to only issue 'regular' single domain certificates.
- 'issuewild' indicates that a wildcard certificate may be issued by the CA.
- 'iodef' allow you to set an email address for failed certificate issuance reports.
- 'ca' indicates which certificate authority (s) have permission to issue certificates.
- It's also possible to set an extra policy for a domain. This enables you to specify that, for instance, only EV SSL certificates may be issued for a specific domain. For example:
CAA 0 issue "www.xolphin.nl; policy=ev"
Because multiple values are possible, multiple CAA records are often required. To generate a CAA record, you can use the following tool: https://sslmate.com/labs/caa/. This tool then returns a DNS (CAA) record that you can copy to your DNS zone. A DNS zone with the simplest form of CAA looks like this:
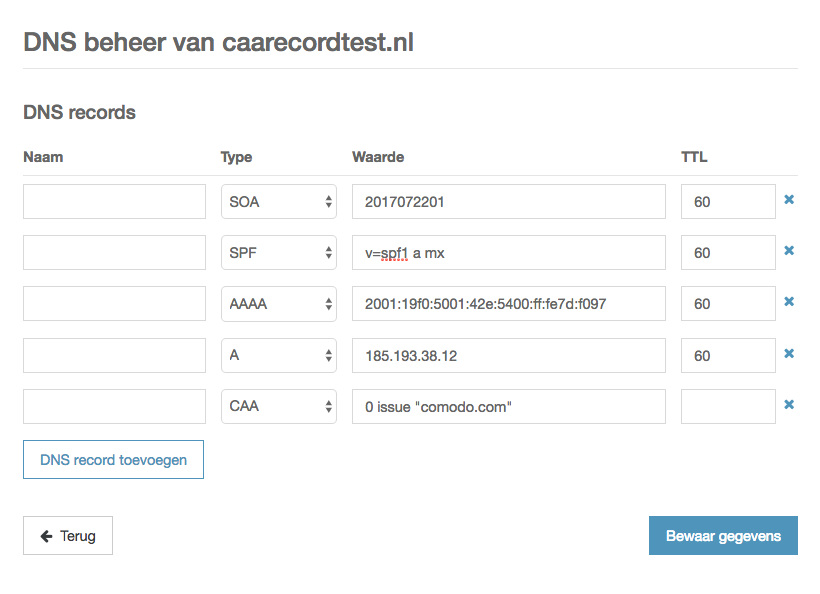
A DNS zone with single CAA record for DV certificates from Comodo, no notifications. It is possible to allow multiple certificate authorities by adding multiple CAA records, as follows:
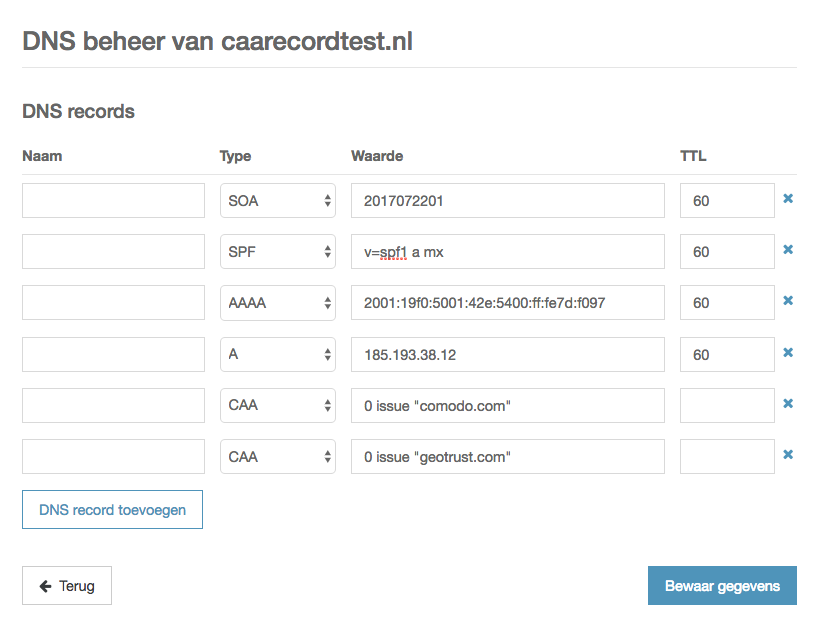
DNS zone with two CAA records, to allow certificate issuance of DV certificates from both Comodo and GeoTrust, no notifications
In order to receive notifications of failed certificate issuance reports, for example, because the certificate should be issued by a certificate authority that is not included in the CAA record, you can add a iodef CAA record:
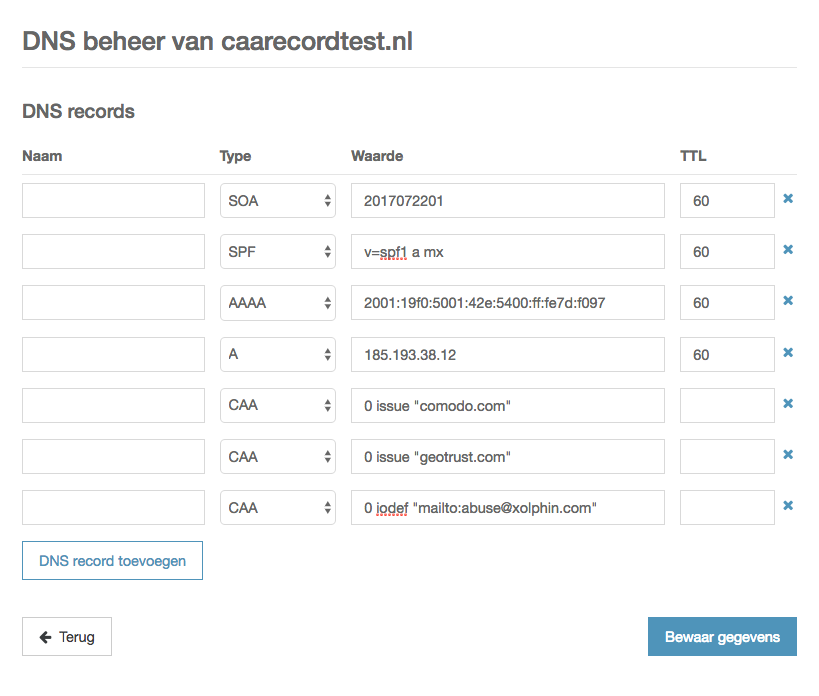
DNS zone with three CAA records, to allow certificate issuance of DV certificates from Comodo and GeoTrust, and reporting to abuse@xolphin.com
By replacing 'issue' on the GeoTrust line with 'issuewild', you enable GeoTrust to issue wildcard certificates, and Comodo only single domain DV certificates. For example, when Comodo tries to issue a wildcard certificate, you will receive a notification on abuse@xolphin.com.
CAA combining with DNSSEC and CT
DNS should be considered an unsafe system because it is theoretically possible for unauthorized entities to customize DNS records. DNSSEC is an additional security layer to prevent this by linking a digital signature to a particular 'DNS zone'. As a result, DNS validity can be structured to prevent abuse. The use of CAA records increases the importance of a secure DNS. If hackers are able to customize the DNS, CAA loses its value because the CAA records can be modified.
CAA also complements Certificate Transparency (CT) :both controlmechanisms serve the same purpose of decreasing the risk 'wrong' certificates are being issued for a specific domain. Where CAA does this before certificate issuance, CT does this after certificate issuance.
SSLCheck
Our SSLCheck will examine your website's root and intermediate certificates for correctness and report any potential issues

